The Multi-Purpose Crew Vehicle(MPCV), or Orion, being assembled and tested at Lockheed Martin's Vertical Testing Facility in Colorado. Drawing from more than 50 years of spaceflight research and development, Orion is designed to meet the evolving needs of our nation's space program for decades to come. As the flagship of our nation's next-generation space fleet, Orion will push the envelope of human spaceflight far beyond low Earth orbit. Orion may resemble its Apollo-era predecessors, but its technology and capability are light years apart. Orion features dozens of technology advancements and innovations that have been incorporated into the spacecraft's subsystem and component design. A test version of the Orion spacecraft makes a stop at the Science Museum Oklahoma in Oklahoma City today, giving residents the chance to see a full scale test version of the vehicle that will take humans into deep space...
Wednesday, January 25, 2012
Monday, October 3, 2011
: Encryption and Decryption Encyclopedia including some Hacking attack techniques :
Algebraic attack
A method of cryptanalytic attack used against block ciphers that exhibit a significant amount of mathematical structure.
Algorithm
Algorithm is a process for completing a task. An encryption algorithm is a mathematical process (mathematical formula), to encrypt and decrypt messages. It typically has two elements: data (for example, plaintext or email message that you want to encrypt or decrypt) and a key. Also see Asymmetric Algorithm and Symmetric Algorithm
Asymmetric Algorithm
Asymmetric Algorithm (also known as public key cryptography) uses two different keys for encryption and decryption. Keys for encryption and decryption are mathematically related, but it is very hard or even impossible to deduce one key from the other. Asymmetric Algorithm is called "public key" because the encryption key can be made public. Anyone can use the public key to encrypt a message, but only the owner of the corresponding private key can decrypt it.
Asymmetric Cryptography
Asymmetric Cryptography (also known as public key cryptography) is encryption software that requires two keys: a public key and a private key. Encryption software users distribute their public key, but keep their private key to themselves. When someone wants to send an encrypted message, the sender uses the recipient's public key to encrypt the message, which can only be decrypted by the person who holds the corresponding private key.
Asymmetric Encryption
Asymmetric encryption (Asymmetric Cipher) uses a seperate key for encryption and decryption. The decryption key is very hard or even impossible to derive from the encryption key. The encryption key is public so that anyone can encrypt a message. However, the decryption key is private, so that only the receiver is able to decrypt the message. It is common to set up a pair of keys within a network so that each user has a public key and a private key. The public key is made available to everyone so that they can send messages, but the private key is only made available to the person it belongs to.
Asymmetric Cipher
Cipher that uses different (not trivially related) keys for encryption and decryption. Also see Asymmetric Encryption
Attack
Either a successful or unsuccessful attempt at breaking part or all of a cryptosystem. Also see algebraic attack, birthday attack, brute force attack, chosen ciphertext attack,chosen plaintext attack, differential cryptanalysis, known plaintext attack, linear cryptanalysis, middleperson attack.
Authentication
Authentication is the process of verifying that a file or message has not been modified in transit from the sender to the recipient(s) or while stored on a computer.
Back door
A "back door" is an alternate, usually secret, method to decrypt an encrypted file or message without the key. This method is usually only known to a few people, such as the author of the program. Software that has a back door is not secure as "back door" greatly reduces the reliability of the implementation of an encryption algorithm.
Birthday attack
A brute-force attack used to find collisions. It gets its name from the surprising result that the probability of two or more people in a group of 23 sharing the same birthday is greater than 1/2.
Block
A fixed-length group of bits
Block Cipher
Block cipher (method for encrypting data in blocks) is a symmetric cipher which encrypts a message by breaking it down into blocks (commonly of 64 bits) and encrypting data in each block. Block Cipher is opposite to encoding bit-by-bit like stream cipher.
Blowfish
Blowfish is a symmetric encryption algorithm - 64-bit block cipher that employs the asymmetric key model. Blowfish was designed in 1993 by Bruce Schneier as a fast, free alternative to existing encryption algorithms. Blowfish has a variable key length - from 32 bits to 448 bits. Since then Blowfish has been analyzed considerably, and is gaining acceptance as a strong encryption algorithm.
Brute Force Attack
Brute Force Attack is a form of attack in which each possibility is tried until success is obtained. Typically, a ciphertext is deciphered under different keys until plaintext is recognized.
CAST
CAST is a popular 64-bit block cipher allowing key sizes up to 128 bits. The name CAST stands for Carlisle Adams and Stafford Tavares, the inventors of CAST.
Certificate
A certificate is a data file that identifies an individual, organization, or business. Certificates are obtained from specialized certificate-issuing companies, and can be used to encrypt data and/or confirm the certificate owner's identity.
Chosen ciphertext attack
An attack where the cryptanalyst may choose the ciphertext to be decrypted.
Chosen plaintext attack
A form of cryptanalysis where the cryptanalyst may choose the plaintext to be encrypted
Cipher
Cipher is a cryptographic algorithm used to encrypt and decrypt files and message (encryption algorithm).
Also see Block cipher and Stream cipher
Ciphertext
This is the encrypted message produced by applying the algorithm to the plaintext message using the secret key.
Ciphertext-only attack
A form of cryptanalysis where the cryptanalyst has some ciphertext but nothing else.
Cleartext
Unencrypted text, a.k.a. plaintext.
Clipper
Clipper is an encryption chip developed and sponsored by the U.S. government as part of the Capstone project.
Cracker
Cracker is someone who attempts to gain unauthorized access to a computer system.
Cryptanalysis
Cryptanalysis is an algorithm or program for testing cryptography for vulnerabilities.
Cryptography
Cryptography is a field of mathematics and computer science concerned with information security and related issues, particularly encryption and authentication.
Cryptography algorithm
A cryptographic algorithm, also known as a cipher, is a mathematical function which uses plaintext as the input and produces ciphertext as the output and vice versa.
Cryptology
Cryptology is the study of both cryptography and cryptanalysis.
Cryptosystem
An encryption decryption algorithm (cipher), together with all possible plaintexts, ciphertexts and keys.
Decryption
Decryption is a process to convert ciphertext back into plaintext.
DES Digital Encryption Standard.
Digital Encryption Standard (DES) is a symmetric block cipher with 64-bit block size that uses using a 56-bit key which was originally developed by the US National Institute of Standards and Technology (NIST) in 1977 as a standard encryption algorithm. Due to recent advances in computer technology, some experts no longer consider DES secure against all attacks; since then Triple-DES (3DES) has emerged as a stronger method. Using standard DES encryption, Triple-DES encrypts data three times and uses a different key for at least one of the three passes giving it a cumulative key size of 112-168 bits. Also see Triple DES
Dictionary attack
A brute force attack that tries passwords and or keys from a precompiled list of values. This is often done as a precomputation attack.
Differential cryptanalysis
A chosen plaintext attack relying on the analysis of the evolution of the differences between two plaintexts.
Diffie-Hellman
Diffie-Hellman is the first public encryption key algorithm (public-key algorithm), invented in 1976, using discrete logarithms in a finite field. Allows two users to exchange a secret key over an insecure medium without any prior secrets.
Digital Signature
A small piece of code that is used to authenticate the sender of data. Digital signatures are created with encryption software for verification purposes. The signature is encrypted with the user's private key and can only be decrypted with the corresponding public key to verify that the signature was really generated by the holder of the private key. See Asymmetric cryptography.
Digital Signature Standard (DSS)
Digital Signature Standard (DSS) is the U.S. government's standard for authenticating a digital signature.
FTP (File Transfer Protocol)
FTP (File Transfer Protocol) - is an old but still widely used method for sending data across the Internet. The protocol itself has no security, so any login and password information is sent as plaintext. This means that if the login/password transmission is intercepted the security of any data stored on the FTP server may be compromised.
Feistel Cipher
The Feistel cipher is a basic block cipher, which was developed by Horst Feistel at IBM. Its particular structure forms the bases of many modern block ciphers. The first Feistel cipher patented was the Lucifer Cipher in 1971.
A Feistel cipher is a product cipher in that it applies the same basic encryption scheme iteratively for several rounds. It works on a block of bits of a set size and applies in each iteration a so called round function, i.e. an encryption function parameterised by a round key. Round keys are often derived from a general key and therefore called sub-keys. They are invoked in the encryption scheme by some function called a Feistel function.
Feistel function
Function applying the round key in the Feistel cipher, thereby effectively parameterising the round function.
Feistel networks
Feistel network is a general way of constructing block ciphers from simple functions. The original idea was used in the block cipher Lucifer, invented by Horst Feistel. Several variations have been devised from the original version. The standard Feistel network takes a function from n bits to n bits and produces an invertible function from 2n bits to 2n bits. The basic function upon which the structure is based is often called the round function. The essential property of Feistel networks that makes them so useful in cipher design is that the round function need not be invertible, but the resulting function always is. If the round function depends on, say, k bits of a key, then the Feistel cipher requires rk bits of the key where r is the number of rounds used. The security of the Feistel structure is not obvious, but analysis of DES has shown that it is a good way to construct ciphers. It is compulsory that a Feistel cipher has enough rounds, but just adding more rounds does not always guarantee security. Encryption
Encryption is the transformation of plaintext into ciphertext through a mathematical process.
Encryption Algorithm
Series of steps that mathematically transforms plaintext or other readable information into unintelligible ciphertext.
International Data Encryption Algorithm (IDEA)
IDEA stands for International Data Encryption Algorithm. IDEA is a block cipher using a symmetric algorithm based on a 128 bit key. This key length makes it impossible to break by simply trying every key. International Data Encryption Algorithm (IDEA) was introduced in 1992 as a potential alternative to DES. IDEA is the data encryption algorithm used in PGP.
DSA
The Digital Signature Algorithm (DSA) is a United States Federal Government standard or FIPS for digital signatures. It was proposed by the National Institute of Standards and Technology (NIST) in August 1991 for use in their Digital Signature Standard (DSS).
Key
Key is a collection of bits which is used to encrypt or decrypt messages, documents or other types of electronic data. The more numbers of bits the key has, the stronger it is to break because there are more possible permutations of data bits. Since bits are binary, the number of possible permutations for a key of is 2 x number of bits. The specific way a key is used depends on whether it's used with asymmetric or symmetric cryptography. See also distributed key, private key, public key, secret key, symmetric key,weak key.
Key Escrow
Key Escrow is a process that requires a copy of all decryption keys be placed into escrow so that encrypted messages may be decrypted as required by a law enforcement agency.
Key exchange
A process used by two or more parties to exchange keys in cryptosystems.
Key management
The various processes that deal with the creation, distribution, authentication, and storage of keys.
Key pair
The full key information in a public-key cryptosystem, consisting of the public key and private key.
Key Schedule
A function to generate round keys from one input key.
Known plaintext attack
A form of cryptanalysis where the cryptanalyst knows both the plaintext and the associated ciphertext.
Linear cryptanalysis
A known plaintext attack that uses linear approximations to describe the behavior of the block cipher. See known plaintext attack.
Lucifer
First simple Feistel cipher.
Meet-in-the-middle attack
A known plaintext attack against double encryption with two separated keys where the attacker encrypts a plaintext with a key and "decrypts" the original ciphertext with another key and hopes to get the same value.
Middleperson attack
A person who intercepts keys and impersonates the intended recipients.
Password
Passwords are keys you use to access personal information you store on your PC and in your accounts. Passwords help to ensure that only authorized users access PC and accounts. Passwords protect personal information we don't want anyone knows.
Permutation Box (P-Box)
An operation that takes a set of input blocks, combines them and applies a permutation.
PGP (Pretty Good Privacy)
PGP (Pretty Good Privacy) - is a public-private key cryptography system which allows for users to more easily integrate the use of encryption in their daily tasks, such as electronic mail protection and authentication, and protecting files stored on a computer. PGP is available for free to individual home users. It was originally designed by Phil Zimmerman. It uses IDEA, CAST or Triple DES for actual data encryption and RSA (with up to 2048-bit key) or DH/DSS (with 1024-bit signature key and 4096-bit encryption key) for key management and digital signatures. The RSA or DH public key is used to encrypt the IDEA secret key as part of the message.
PKAF
Public Key Authentication Framework (PKAF) is a system for authenticating digital signatures based on a hierarchy of trusted signatures.
Plaintext
Plaintext is unencrypted text (cleartext), the original message or filet o which an encryption algorithm is applied.
Precomputation attack
An attack where the adversary precomputes a look-up table of values used to crack encryption or passwords. See also dictionary attack.
Prime number
Any integer greater than 1 that is divisible only by 1 and itself.
Private Key
Private key is a secret key of a public-private key cryptography system (it is used in asymmetric cryptography). The Private Key is normally known only to the key owner. Messages are encrypted using the Public Key and can be decrypted by the owner of the corresponding Private Key. For digital signatures, however, a document is signed with a Private Key and authenticated with the corresponding Public Key. Private keys should not be distributed. Also see Asymmetric cryptography.
Product cipher
Cipher that applies the same basic encryption scheme iteratively forseveral rounds.
Public Key
Public keys is the public key of a public-private key cryptography system. Public key is used in asymmetric cryptography. Public keys are used to enable someone to encrypt messages intended for the owner of the public key. Public keys are meant for distribution, so anyone who wants to send an encrypted message to the owner of the public key can do so, but only the owner of the corresponding private key can decrypt the message. Also see Asymmetric cryptography.
Public-key Cryptography
Cryptography based on methods involving a public key and a private key.
Public-key algorithms
Public-key algorithms (also known as Asymmetric algorithms) use two different keys (a key pair) for encryption and decryption: a public key and a private key. Encryption software users distribute their public key, but keep their private key to themselves. When someone wants to send an encrypted message, the sender uses the recipient's public key to encrypt the message, which can only be decrypted by the person who holds the corresponding private key.
RC2
RC2 is a variable-key-length cipher. It was invented by Ron Rivest for RSA Data Security, Inc. Its details have not been published.
RC4
RC4 was developed by Ron Rivest in 1987. It is a variable-key-size stream cipher. It is a cipher with a key size of up to 2048 bits (256 bytes).
RC6
RC6 is a symmetric key block cipher derived from RC5. It was designed by Ron Rivest, Matt Robshaw, Ray Sidney, and Yiqun Lisa Yin to meet the requirements of the Advanced Encryption Standard (AES) competition. RC6 encryption algorithm was selected among the other finalists to become the new federal Advanced Encryption Standard (AES).
Round function
The parameterised encryption function applied during one round of Feistel cipher.
RSA
RSA is the best known public key algorithm, named after its inventors: Rivest, Shamir and Adleman. RSA uses public and private keys that are functions of a pair of large prime numbers. Its security is based on the difficulty of factoring large integers. The RSA algorithm can be used for both public key encryption and digital signatures. The keys used for encryption and decryption in RSA algorithm, are generated using random data. The key used for encryption is a public key and the key used for decryption is a private key. Public keys are stored anywhere publicly accessible. The sender of message encrypts the data using public key, and the receiver decrypts it using his/her own private key. That way, no one else can intercept the data except receiver.
Encryption is done with a public key(or private key for signature). Decryption is done with a private key (or public key to verify signature).
Salt
A string of random (or pseudorandom) bits concatenated with a key or password to foil precomputation attacks.
Secret Key
Secret Key is the the input for the algorithm. A secret key can be a number, a word, or just a string of random letters. Secret key is applied to the information to change the content in a particular way.
Signature
See Digital Signature
Symmetric algorithms
Symmetric algorithms use the same key for Encryption and Decryption. Symmetric algorithms require that both the sender and the receiver agree on a key before they can exchange messages securely. Some symmetric algorithms (Stream Ciphers) operate on 1 bit (or sometimes 1 byte) of plaintext at a time (encrypt data bit-by-bit). Other symmetric algorithms (Block Ciphers) operate on blocks of bits at a time - encrypts a message by breaking it down into blocks (commonly of 64 bits) and encrypting data in each block.
Symmetric Cryptography
Symmetric Cryptography is a method of encryption in which the same key is used for Encryption and Decryption. The sender and receiver have to agree on a key before they can communicate securely.
Symmetric Encryption
Symmetric encryption uses a secret key value to encrypt and decrypt data. Both the sender and receiver need the same key to encrypt or decrypt. There are two types of symmetric algorithms: stream algorithms and block algorithms. The stream algorithm works on one bit or byte at a time, whereas the block algorithm works on larger blocks of data (typically 64 bits). The drawback to this type of system is that if the key is discovered, all messages can be decrypted.
Symmetric Key
Symmetric Key is the key that is used to for both encrypting and decrypting a file or a message.
SSH (Secure Shell)
SSH (Secure Shell) is a protocol that allows someone using one computer to remotely operate another computer. Unlike Telnet, however, it uses secure (encrypted) transmissions.
Steganography
Steganography is the process of hiding data inside other data. For example, a text file could be hidden "inside" an image or a sound file. By looking at the image, or listening to the sound, you would not know that there is extra information present.
Stream Cipher
Stream cipher is a symmetric cipher which encrypts data bit-by-bit. Stream Cipher is opposite to a block cipher.
Substitution
Substitution means replacing symbols or group of symbols by other symbols or groups of symbols. Substitution without transposition doesn't provide sufficient security, but strong ciphers can be built by combining them.
Substitution Box
Substitution Box (S-Box) is a lookup table that substitutes n-bit block for m-bit block.
Substitution-Permutation Network (SPN)
Substitution-Permutation Network (SPN) is a cipher composed of a number of stages, each involving substitutions and permutations. Well known examples of SPNs are DESand CAST-128.
Telnet
Telnet is a protocol that allows someone using one computer to remotely operate another computer. Telnet, like FTP, is not secure. Security is possible by using special Telnet server/client software or an alternative protocol (like SSH).
Transposition
Transposition, on the other hand, means permuting the symbols in a block. Transposition without substitution doesn't provide sufficient security, but strong ciphers can be built by combining them.
Triple DES
Triple DES is a method of improving the strength of the DES algorithm by using it three times in sequence with different keys. Triple DES uses a 64-bit key consisting of 56 effective key bits and 8 parity bits. The size of the block for Triple DES is 8 bytes. Triple-DES encrypts the data in 8-byte chunks.
A method of cryptanalytic attack used against block ciphers that exhibit a significant amount of mathematical structure.
Algorithm
Algorithm is a process for completing a task. An encryption algorithm is a mathematical process (mathematical formula), to encrypt and decrypt messages. It typically has two elements: data (for example, plaintext or email message that you want to encrypt or decrypt) and a key. Also see Asymmetric Algorithm and Symmetric Algorithm
Asymmetric Algorithm
Asymmetric Algorithm (also known as public key cryptography) uses two different keys for encryption and decryption. Keys for encryption and decryption are mathematically related, but it is very hard or even impossible to deduce one key from the other. Asymmetric Algorithm is called "public key" because the encryption key can be made public. Anyone can use the public key to encrypt a message, but only the owner of the corresponding private key can decrypt it.
Asymmetric Cryptography
Asymmetric Cryptography (also known as public key cryptography) is encryption software that requires two keys: a public key and a private key. Encryption software users distribute their public key, but keep their private key to themselves. When someone wants to send an encrypted message, the sender uses the recipient's public key to encrypt the message, which can only be decrypted by the person who holds the corresponding private key.
Asymmetric Encryption
Asymmetric encryption (Asymmetric Cipher) uses a seperate key for encryption and decryption. The decryption key is very hard or even impossible to derive from the encryption key. The encryption key is public so that anyone can encrypt a message. However, the decryption key is private, so that only the receiver is able to decrypt the message. It is common to set up a pair of keys within a network so that each user has a public key and a private key. The public key is made available to everyone so that they can send messages, but the private key is only made available to the person it belongs to.
Asymmetric Cipher
Cipher that uses different (not trivially related) keys for encryption and decryption. Also see Asymmetric Encryption
Attack
Either a successful or unsuccessful attempt at breaking part or all of a cryptosystem. Also see algebraic attack, birthday attack, brute force attack, chosen ciphertext attack,chosen plaintext attack, differential cryptanalysis, known plaintext attack, linear cryptanalysis, middleperson attack.
Authentication
Authentication is the process of verifying that a file or message has not been modified in transit from the sender to the recipient(s) or while stored on a computer.
Back door
A "back door" is an alternate, usually secret, method to decrypt an encrypted file or message without the key. This method is usually only known to a few people, such as the author of the program. Software that has a back door is not secure as "back door" greatly reduces the reliability of the implementation of an encryption algorithm.
Birthday attack
A brute-force attack used to find collisions. It gets its name from the surprising result that the probability of two or more people in a group of 23 sharing the same birthday is greater than 1/2.
Block
A fixed-length group of bits
Block Cipher
Block cipher (method for encrypting data in blocks) is a symmetric cipher which encrypts a message by breaking it down into blocks (commonly of 64 bits) and encrypting data in each block. Block Cipher is opposite to encoding bit-by-bit like stream cipher.
Blowfish
Blowfish is a symmetric encryption algorithm - 64-bit block cipher that employs the asymmetric key model. Blowfish was designed in 1993 by Bruce Schneier as a fast, free alternative to existing encryption algorithms. Blowfish has a variable key length - from 32 bits to 448 bits. Since then Blowfish has been analyzed considerably, and is gaining acceptance as a strong encryption algorithm.
Brute Force Attack
Brute Force Attack is a form of attack in which each possibility is tried until success is obtained. Typically, a ciphertext is deciphered under different keys until plaintext is recognized.
CAST
CAST is a popular 64-bit block cipher allowing key sizes up to 128 bits. The name CAST stands for Carlisle Adams and Stafford Tavares, the inventors of CAST.
Certificate
A certificate is a data file that identifies an individual, organization, or business. Certificates are obtained from specialized certificate-issuing companies, and can be used to encrypt data and/or confirm the certificate owner's identity.
Chosen ciphertext attack
An attack where the cryptanalyst may choose the ciphertext to be decrypted.
Chosen plaintext attack
A form of cryptanalysis where the cryptanalyst may choose the plaintext to be encrypted
Cipher
Cipher is a cryptographic algorithm used to encrypt and decrypt files and message (encryption algorithm).
Also see Block cipher and Stream cipher
Ciphertext
This is the encrypted message produced by applying the algorithm to the plaintext message using the secret key.
Ciphertext-only attack
A form of cryptanalysis where the cryptanalyst has some ciphertext but nothing else.
Cleartext
Unencrypted text, a.k.a. plaintext.
Clipper
Clipper is an encryption chip developed and sponsored by the U.S. government as part of the Capstone project.
Cracker
Cracker is someone who attempts to gain unauthorized access to a computer system.
Cryptanalysis
Cryptanalysis is an algorithm or program for testing cryptography for vulnerabilities.
Cryptography
Cryptography is a field of mathematics and computer science concerned with information security and related issues, particularly encryption and authentication.
Cryptography algorithm
A cryptographic algorithm, also known as a cipher, is a mathematical function which uses plaintext as the input and produces ciphertext as the output and vice versa.
Cryptology
Cryptology is the study of both cryptography and cryptanalysis.
Cryptosystem
An encryption decryption algorithm (cipher), together with all possible plaintexts, ciphertexts and keys.
Decryption
Decryption is a process to convert ciphertext back into plaintext.
DES Digital Encryption Standard.
Digital Encryption Standard (DES) is a symmetric block cipher with 64-bit block size that uses using a 56-bit key which was originally developed by the US National Institute of Standards and Technology (NIST) in 1977 as a standard encryption algorithm. Due to recent advances in computer technology, some experts no longer consider DES secure against all attacks; since then Triple-DES (3DES) has emerged as a stronger method. Using standard DES encryption, Triple-DES encrypts data three times and uses a different key for at least one of the three passes giving it a cumulative key size of 112-168 bits. Also see Triple DES
Dictionary attack
A brute force attack that tries passwords and or keys from a precompiled list of values. This is often done as a precomputation attack.
Differential cryptanalysis
A chosen plaintext attack relying on the analysis of the evolution of the differences between two plaintexts.
Diffie-Hellman
Diffie-Hellman is the first public encryption key algorithm (public-key algorithm), invented in 1976, using discrete logarithms in a finite field. Allows two users to exchange a secret key over an insecure medium without any prior secrets.
Digital Signature
A small piece of code that is used to authenticate the sender of data. Digital signatures are created with encryption software for verification purposes. The signature is encrypted with the user's private key and can only be decrypted with the corresponding public key to verify that the signature was really generated by the holder of the private key. See Asymmetric cryptography.
Digital Signature Standard (DSS)
Digital Signature Standard (DSS) is the U.S. government's standard for authenticating a digital signature.
FTP (File Transfer Protocol)
FTP (File Transfer Protocol) - is an old but still widely used method for sending data across the Internet. The protocol itself has no security, so any login and password information is sent as plaintext. This means that if the login/password transmission is intercepted the security of any data stored on the FTP server may be compromised.
Feistel Cipher
The Feistel cipher is a basic block cipher, which was developed by Horst Feistel at IBM. Its particular structure forms the bases of many modern block ciphers. The first Feistel cipher patented was the Lucifer Cipher in 1971.
A Feistel cipher is a product cipher in that it applies the same basic encryption scheme iteratively for several rounds. It works on a block of bits of a set size and applies in each iteration a so called round function, i.e. an encryption function parameterised by a round key. Round keys are often derived from a general key and therefore called sub-keys. They are invoked in the encryption scheme by some function called a Feistel function.
Feistel function
Function applying the round key in the Feistel cipher, thereby effectively parameterising the round function.
Feistel networks
Feistel network is a general way of constructing block ciphers from simple functions. The original idea was used in the block cipher Lucifer, invented by Horst Feistel. Several variations have been devised from the original version. The standard Feistel network takes a function from n bits to n bits and produces an invertible function from 2n bits to 2n bits. The basic function upon which the structure is based is often called the round function. The essential property of Feistel networks that makes them so useful in cipher design is that the round function need not be invertible, but the resulting function always is. If the round function depends on, say, k bits of a key, then the Feistel cipher requires rk bits of the key where r is the number of rounds used. The security of the Feistel structure is not obvious, but analysis of DES has shown that it is a good way to construct ciphers. It is compulsory that a Feistel cipher has enough rounds, but just adding more rounds does not always guarantee security. Encryption
Encryption is the transformation of plaintext into ciphertext through a mathematical process.
Encryption Algorithm
Series of steps that mathematically transforms plaintext or other readable information into unintelligible ciphertext.
International Data Encryption Algorithm (IDEA)
IDEA stands for International Data Encryption Algorithm. IDEA is a block cipher using a symmetric algorithm based on a 128 bit key. This key length makes it impossible to break by simply trying every key. International Data Encryption Algorithm (IDEA) was introduced in 1992 as a potential alternative to DES. IDEA is the data encryption algorithm used in PGP.
DSA
The Digital Signature Algorithm (DSA) is a United States Federal Government standard or FIPS for digital signatures. It was proposed by the National Institute of Standards and Technology (NIST) in August 1991 for use in their Digital Signature Standard (DSS).
Key
Key is a collection of bits which is used to encrypt or decrypt messages, documents or other types of electronic data. The more numbers of bits the key has, the stronger it is to break because there are more possible permutations of data bits. Since bits are binary, the number of possible permutations for a key of is 2 x number of bits. The specific way a key is used depends on whether it's used with asymmetric or symmetric cryptography. See also distributed key, private key, public key, secret key, symmetric key,weak key.
Key Escrow
Key Escrow is a process that requires a copy of all decryption keys be placed into escrow so that encrypted messages may be decrypted as required by a law enforcement agency.
Key exchange
A process used by two or more parties to exchange keys in cryptosystems.
Key management
The various processes that deal with the creation, distribution, authentication, and storage of keys.
Key pair
The full key information in a public-key cryptosystem, consisting of the public key and private key.
Key Schedule
A function to generate round keys from one input key.
Known plaintext attack
A form of cryptanalysis where the cryptanalyst knows both the plaintext and the associated ciphertext.
Linear cryptanalysis
A known plaintext attack that uses linear approximations to describe the behavior of the block cipher. See known plaintext attack.
Lucifer
First simple Feistel cipher.
Meet-in-the-middle attack
A known plaintext attack against double encryption with two separated keys where the attacker encrypts a plaintext with a key and "decrypts" the original ciphertext with another key and hopes to get the same value.
Middleperson attack
A person who intercepts keys and impersonates the intended recipients.
Password
Passwords are keys you use to access personal information you store on your PC and in your accounts. Passwords help to ensure that only authorized users access PC and accounts. Passwords protect personal information we don't want anyone knows.
Permutation Box (P-Box)
An operation that takes a set of input blocks, combines them and applies a permutation.
PGP (Pretty Good Privacy)
PGP (Pretty Good Privacy) - is a public-private key cryptography system which allows for users to more easily integrate the use of encryption in their daily tasks, such as electronic mail protection and authentication, and protecting files stored on a computer. PGP is available for free to individual home users. It was originally designed by Phil Zimmerman. It uses IDEA, CAST or Triple DES for actual data encryption and RSA (with up to 2048-bit key) or DH/DSS (with 1024-bit signature key and 4096-bit encryption key) for key management and digital signatures. The RSA or DH public key is used to encrypt the IDEA secret key as part of the message.
PKAF
Public Key Authentication Framework (PKAF) is a system for authenticating digital signatures based on a hierarchy of trusted signatures.
Plaintext
Plaintext is unencrypted text (cleartext), the original message or filet o which an encryption algorithm is applied.
Precomputation attack
An attack where the adversary precomputes a look-up table of values used to crack encryption or passwords. See also dictionary attack.
Prime number
Any integer greater than 1 that is divisible only by 1 and itself.
Private Key
Private key is a secret key of a public-private key cryptography system (it is used in asymmetric cryptography). The Private Key is normally known only to the key owner. Messages are encrypted using the Public Key and can be decrypted by the owner of the corresponding Private Key. For digital signatures, however, a document is signed with a Private Key and authenticated with the corresponding Public Key. Private keys should not be distributed. Also see Asymmetric cryptography.
Product cipher
Cipher that applies the same basic encryption scheme iteratively forseveral rounds.
Public Key
Public keys is the public key of a public-private key cryptography system. Public key is used in asymmetric cryptography. Public keys are used to enable someone to encrypt messages intended for the owner of the public key. Public keys are meant for distribution, so anyone who wants to send an encrypted message to the owner of the public key can do so, but only the owner of the corresponding private key can decrypt the message. Also see Asymmetric cryptography.
Public-key Cryptography
Cryptography based on methods involving a public key and a private key.
Public-key algorithms
Public-key algorithms (also known as Asymmetric algorithms) use two different keys (a key pair) for encryption and decryption: a public key and a private key. Encryption software users distribute their public key, but keep their private key to themselves. When someone wants to send an encrypted message, the sender uses the recipient's public key to encrypt the message, which can only be decrypted by the person who holds the corresponding private key.
RC2
RC2 is a variable-key-length cipher. It was invented by Ron Rivest for RSA Data Security, Inc. Its details have not been published.
RC4
RC4 was developed by Ron Rivest in 1987. It is a variable-key-size stream cipher. It is a cipher with a key size of up to 2048 bits (256 bytes).
RC6
RC6 is a symmetric key block cipher derived from RC5. It was designed by Ron Rivest, Matt Robshaw, Ray Sidney, and Yiqun Lisa Yin to meet the requirements of the Advanced Encryption Standard (AES) competition. RC6 encryption algorithm was selected among the other finalists to become the new federal Advanced Encryption Standard (AES).
Round function
The parameterised encryption function applied during one round of Feistel cipher.
RSA
RSA is the best known public key algorithm, named after its inventors: Rivest, Shamir and Adleman. RSA uses public and private keys that are functions of a pair of large prime numbers. Its security is based on the difficulty of factoring large integers. The RSA algorithm can be used for both public key encryption and digital signatures. The keys used for encryption and decryption in RSA algorithm, are generated using random data. The key used for encryption is a public key and the key used for decryption is a private key. Public keys are stored anywhere publicly accessible. The sender of message encrypts the data using public key, and the receiver decrypts it using his/her own private key. That way, no one else can intercept the data except receiver.
Encryption is done with a public key(or private key for signature). Decryption is done with a private key (or public key to verify signature).
Salt
A string of random (or pseudorandom) bits concatenated with a key or password to foil precomputation attacks.
Secret Key
Secret Key is the the input for the algorithm. A secret key can be a number, a word, or just a string of random letters. Secret key is applied to the information to change the content in a particular way.
Signature
See Digital Signature
Symmetric algorithms
Symmetric algorithms use the same key for Encryption and Decryption. Symmetric algorithms require that both the sender and the receiver agree on a key before they can exchange messages securely. Some symmetric algorithms (Stream Ciphers) operate on 1 bit (or sometimes 1 byte) of plaintext at a time (encrypt data bit-by-bit). Other symmetric algorithms (Block Ciphers) operate on blocks of bits at a time - encrypts a message by breaking it down into blocks (commonly of 64 bits) and encrypting data in each block.
Symmetric Cryptography
Symmetric Cryptography is a method of encryption in which the same key is used for Encryption and Decryption. The sender and receiver have to agree on a key before they can communicate securely.
Symmetric Encryption
Symmetric encryption uses a secret key value to encrypt and decrypt data. Both the sender and receiver need the same key to encrypt or decrypt. There are two types of symmetric algorithms: stream algorithms and block algorithms. The stream algorithm works on one bit or byte at a time, whereas the block algorithm works on larger blocks of data (typically 64 bits). The drawback to this type of system is that if the key is discovered, all messages can be decrypted.
Symmetric Key
Symmetric Key is the key that is used to for both encrypting and decrypting a file or a message.
SSH (Secure Shell)
SSH (Secure Shell) is a protocol that allows someone using one computer to remotely operate another computer. Unlike Telnet, however, it uses secure (encrypted) transmissions.
Steganography
Steganography is the process of hiding data inside other data. For example, a text file could be hidden "inside" an image or a sound file. By looking at the image, or listening to the sound, you would not know that there is extra information present.
Stream Cipher
Stream cipher is a symmetric cipher which encrypts data bit-by-bit. Stream Cipher is opposite to a block cipher.
Substitution
Substitution means replacing symbols or group of symbols by other symbols or groups of symbols. Substitution without transposition doesn't provide sufficient security, but strong ciphers can be built by combining them.
Substitution Box
Substitution Box (S-Box) is a lookup table that substitutes n-bit block for m-bit block.
Substitution-Permutation Network (SPN)
Substitution-Permutation Network (SPN) is a cipher composed of a number of stages, each involving substitutions and permutations. Well known examples of SPNs are DESand CAST-128.
Telnet
Telnet is a protocol that allows someone using one computer to remotely operate another computer. Telnet, like FTP, is not secure. Security is possible by using special Telnet server/client software or an alternative protocol (like SSH).
Transposition
Transposition, on the other hand, means permuting the symbols in a block. Transposition without substitution doesn't provide sufficient security, but strong ciphers can be built by combining them.
Triple DES
Triple DES is a method of improving the strength of the DES algorithm by using it three times in sequence with different keys. Triple DES uses a 64-bit key consisting of 56 effective key bits and 8 parity bits. The size of the block for Triple DES is 8 bytes. Triple-DES encrypts the data in 8-byte chunks.
Labels:
Tech
Saturday, September 17, 2011
SSL and Certificates
A very warm Hello to All once again after a long days :)
Many of you may noticed a Green SSL Lock Mark (Like above :) )on your browser's address bar while using Net Banking , google secure (https://encrypted.google.com/), routed to any Payment Gateway, secure Facebook or many of the government websites apart from that many times we've seen for an unsecured Web-Page or the web or IP device with expired security certificates will show the following icon.
So now what is SSL and its security certificates?
lets have a look:
Many of you may noticed a Green SSL Lock Mark (Like above :) )on your browser's address bar while using Net Banking , google secure (https://encrypted.google.com/), routed to any Payment Gateway, secure Facebook or many of the government websites apart from that many times we've seen for an unsecured Web-Page or the web or IP device with expired security certificates will show the following icon.

lets have a look:
The Secure Socket Layer protocol was created by Netscape to ensure secure transactions between web servers and browsers. The protocol uses a third party, a Certificate Authority (CA), to identify one end or both end of the transactions. This is in short how it works.
- A browser requests a secure page (usually https://).
- The web server sends its public key with its certificate.
- The browser checks that the certificate was issued by a trusted party (usually a trusted root CA), that the certificate is still valid and that the certificate is related to the site contacted.
- The browser then uses the public key, to encrypt a random symmetric encryption key and sends it to the server with the encrypted URL required as well as other encrypted http data.
- The web server decrypts the symmetric encryption key using its private key and uses the symmetric key to decrypt the URL and http data.
- The web server sends back the requested html document and http data encrypted with the symmetric key.
- The browser decrypts the http data and html document using the symmetric key and displays the information.
Several concepts have to be understood here. :)
Private Key/Public Key:
The encryption using a private key/public key pair ensures that the data can be encrypted by one key but can only be decrypted by the other key pair. This is sometime hard to understand, but believe me it works. The keys are similar in nature and can be used alternatively: what one key emcrypts, the other key pair can decrypt. The key pair is based on prime numbers and their length in terms of bits ensures the difficulty of being able to decrypt the message without the key pairs. The trick in a key pair is to keep one key secret (the private key) and to distribute the other key (the public key) to everybody. Anybody can send you an encrypted message, that only you will be able to decrypt. You are the only one to have the other key pair, right? In the opposite , you can certify that a message is only coming from you, because you have encrypted it with you private key, and only the associated public key will decrypt it correctly. Beware, in this case the message is not secured you have only signed it. Everybody has the public key, remember!
One of the problem left is to know the public key of your correspondent. Usually you will ask him to send you a non confidential signed message that will contains his publick key as well as a certificate.
Message-->[Public Key]-->Encrypted Message-->[Private Key]-->Message
|
The Certificate:
How do you know that you are dealing with the right person or rather the right web site. Well, someone has taken great length (if they are serious) to ensure that the web site owners are who they claim to be. This someone, you have to implicitly trust: you have his/her certificate loaded in your browser (a root Certificate). A certificate, contains information about the owner of the certificate, like e-mail address, owner's name, certificate usage, duration of validity, resource location or Distinguished Name (DN) which includes the Common Name (CN) (web site address or e-mail address depending of the usage) and the certificate ID of the person who certifies (signs) this information. It contains also the public key and finally a hash to ensure that the certificate has not been tampered with. As you made the choice to trust the person who signs this certificate, therefore you also trust this certificate. This is a certificate trust tree or certificate path. Usually your browser or application has already loaded the root certificate of well known Certification Authorities (CA) or root CA Certificates. The CA maintains a list of all signed certificates as well as a list of revoked certificates. A certificate is insecure until it is signed, as only a signed certificate cannot be modified. You can sign a certificate using itself, it is called a self signed certificate. All root CA certificates are self signed.
Certificate:
Data:
Version: 3 (0x2)
Serial Number: 1 (0x1)
Signature Algorithm: md5WithRSAEncryption
Issuer: C=FJ, ST=Fiji, L=Suva, O=SOPAC, OU=ICT, CN=SOPAC Root CA/Email=administrator@sopac.org
Validity
Not Before: Nov 20 05:47:44 2001 GMT
Not After : Nov 20 05:47:44 2002 GMT
Subject: C=FJ, ST=Fiji, L=Suva, O=SOPAC, OU=ICT, CN=www.sopac.org/Email=administrator@sopac.org
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public Key: (1024 bit)
Modulus (1024 bit):
00:ba:54:2c:ab:88:74:aa:6b:35:a5:a9:c1:d0:5a:
9b:fb:6b:b5:71:bc:ef:d3:ab:15:cc:5b:75:73:36:
b8:01:d1:59:3f:c1:88:c0:33:91:04:f1:bf:1a:b4:
7a:c8:39:c2:89:1f:87:0f:91:19:81:09:46:0c:86:
08:d8:75:c4:6f:5a:98:4a:f9:f8:f7:38:24:fc:bd:
94:24:37:ab:f1:1c:d8:91:ee:fb:1b:9f:88:ba:25:
da:f6:21:7f:04:32:35:17:3d:36:1c:fb:b7:32:9e:
42:af:77:b6:25:1c:59:69:af:be:00:a1:f8:b0:1a:
6c:14:e2:ae:62:e7:6b:30:e9
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
FE:04:46:ED:A0:15:BE:C1:4B:59:03:F8:2D:0D:ED:2A:E0:ED:F9:2F
X509v3 Authority Key Identifier:
keyid:E6:12:7C:3D:A1:02:E5:BA:1F:DA:9E:37:BE:E3:45:3E:9B:AE:E5:A6
DirName:/C=FJ/ST=Fiji/L=Suva/O=SOPAC/OU=ICT/CN=SOPAC Root CA/Email=administrator@sopac.org
serial:00
Signature Algorithm: md5WithRSAEncryption
34:8d:fb:65:0b:85:5b:e2:44:09:f0:55:31:3b:29:2b:f4:fd:
aa:5f:db:b8:11:1a:c6:ab:33:67:59:c1:04:de:34:df:08:57:
2e:c6:60:dc:f7:d4:e2:f1:73:97:57:23:50:02:63:fc:78:96:
34:b3:ca:c4:1b:c5:4c:c8:16:69:bb:9c:4a:7e:00:19:48:62:
e2:51:ab:3a:fa:fd:88:cd:e0:9d:ef:67:50:da:fe:4b:13:c5:
0c:8c:fc:ad:6e:b5:ee:40:e3:fd:34:10:9f:ad:34:bd:db:06:
ed:09:3d:f2:a6:81:22:63:16:dc:ae:33:0c:70:fd:0a:6c:af:
bc:5a
-----BEGIN CERTIFICATE-----
MIIDoTCCAwqgAwIBAgIBATANBgkqhkiG9w0BAQQFADCBiTELMAkGA1UEBhMCRkox
DTALBgNVBAgTBEZpamkxDTALBgNVBAcTBFN1dmExDjAMBgNVBAoTBVNPUEFDMQww
CgYDVQQLEwNJQ1QxFjAUBgNVBAMTDVNPUEFDIFJvb3QgQ0ExJjAkBgkqhkiG9w0B
CQEWF2FkbWluaXN0cmF0b3JAc29wYWMub3JnMB4XDTAxMTEyMDA1NDc0NFoXDTAy
MTEyMDA1NDc0NFowgYkxCzAJBgNVBAYTAkZKMQ0wCwYDVQQIEwRGaWppMQ0wCwYD
VQQHEwRTdXZhMQ4wDAYDVQQKEwVTT1BBQzEMMAoGA1UECxMDSUNUMRYwFAYDVQQD
Ew13d3cuc29wYWMub3JnMSYwJAYJKoZIhvcNAQkBFhdhZG1pbmlzdHJhdG9yQHNv
cGFjLm9yZzCBnzANBgkqhkiG9w0BAQEFAAOBjQAwgYkCgYEAulQsq4h0qms1panB
0Fqb+2u1cbzv06sVzFt1cza4AdFZP8GIwDORBPG/GrR6yDnCiR+HD5EZgQlGDIYI
2HXEb1qYSvn49zgk/L2UJDer8RzYke77G5+IuiXa9iF/BDI1Fz02HPu3Mp5Cr3e2
JRxZaa++AKH4sBpsFOKuYudrMOkCAwEAAaOCARUwggERMAkGA1UdEwQCMAAwLAYJ
YIZIAYb4QgENBB8WHU9wZW5TU0wgR2VuZXJhdGVkIENlcnRpZmljYXRlMB0GA1Ud
DgQWBBT+BEbtoBW+wUtZA/gtDe0q4O35LzCBtgYDVR0jBIGuMIGrgBTmEnw9oQLl
uh/anje+40U+m67lpqGBj6SBjDCBiTELMAkGA1UEBhMCRkoxDTALBgNVBAgTBEZp
amkxDTALBgNVBAcTBFN1dmExDjAMBgNVBAoTBVNPUEFDMQwwCgYDVQQLEwNJQ1Qx
FjAUBgNVBAMTDVNPUEFDIFJvb3QgQ0ExJjAkBgkqhkiG9w0BCQEWF2FkbWluaXN0
cmF0b3JAc29wYWMub3JnggEAMA0GCSqGSIb3DQEBBAUAA4GBADSN+2ULhVviRAnw
VTE7KSv0/apf27gRGsarM2dZwQTeNN8IVy7GYNz31OLxc5dXI1ACY/x4ljSzysQb
xUzIFmm7nEp+ABlIYuJRqzr6/YjN4J3vZ1Da/ksTxQyM/K1ute5A4/00EJ+tNL3b
Bu0JPfKmgSJjFtyuMwxw/Qpsr7xa
-----END CERTIFICATE-----
|
As You may have noticed, the certificate contains the reference to the issuer, the public key of the owner of this certificate, the dates of validity of this certificate and the signature of the certificate to ensure this certificate hasen't been tampered with. The certificate does not contain the private key as it should never be transmitted in any form whatsoever. This certificate has all the elements to send an encrypted message to the owner (using the public key) or to verify a message signed by the author of this certificate.
The Symmetric key:
Well, Private Key/Public Key encryption algorithms are great, but they are not usually practical. It is asymmetric because you need the other key pair to decrypt. You can't use the same key to encrypt and decrypt. An algorithm using the same key to decrypt and encrypt is deemed to have a symmetric key. A symmetric algorithm is much faster in doing its job than an asymmetric algorithm. But a symmetric key is potentially highly insecure. If the enemy gets hold of the key then you have no more secret information. You must therefore transmit the key to the other party without the enemy getting its hands on it. As you know, nothing is secure on the Internet. The solution is to encapsulate the symmetric key inside a message encrypted with an asymmetric algorithm. You have never transmitted your private key to anybody, then the message encrypted with the public key is secure (relatively secure, nothing is certain except death and taxes). The symmetric key is also chosen randomly, so that if the symmetric secret key is discovered then the next transaction will be totally different.
Symetric Key-->[Public Key]-->Encrypted Symetric Key-->[Private Key]-->Symetric Key
|
Encryption algorithm:
There are several encryption algorithms available, using symmetric or asymmetric methods, with keys of various lengths. Usually, algorithms cannot be patented, if Henri Poincare had patented his algorithms, then he would have been able to sue Albert Einstein... So algorithms cannot be patented except mainly in USA. OpenSSL is developed in a country where algorithms cannot be patented and where encryption technology is not reserved to state agencies like military and secret services. During the negotiation between browser and web server, the applications will indicate to each other a list of algorithms that can be understood ranked by order of preference. The common preferred algorithm is then chosen. OpenSSL can be compiled with or without certain algorithms, so that it can be used in many countries where restrictions apply.
1.2.5. The Hash:
A hash is a number given by a hash function from a message. This is a one way function, it means that it is impossible to get the original message knowing the hash. However the hash will drastically change even for the slightest modification in the message. It is therefore extremely difficult to modify a message while keeping its original hash. It is also called a message digest. Hash functions are used in password mechanisms, in certifying that applications are original (MD5 sum), and in general in ensuring that any message has not been tampered with. It seems that the Internet Enginering Task Force (IETF) prefers SHA1 over MD5 for a number of technical reasons (Cf RFC2459 7.1.2 and 7.1.3).Signing:
Signing a message, means authentifying that you have yourself assured the authenticity of the message (most of the time it means you are the author, but not neccesarily). The message can be a text message, or someone else's certificate. To sign a message, you create its hash, and then encrypt the hash with your private key, you then add the encrypted hash and your signed certificate with the message. The recipient will recreate the message hash, decrypts the encrypted hash using your well known public key stored in your signed certificate, check that both hash are equals and finally check the certificate.
The other advantage of signing your messages is that you transmit your public key and certificate automatically to all your recipients.
There are usually 2 ways to sign, encapsulating the text message inside the signature (with delimiters), or encoding the message altogether with the signature. This later form is a very simple encryption form as any software can decrypt it if it can read the embedded public key. The advantage of the first form is that the message is human readable allowing any non complaint client to pass the message as is for the user to read, while the second form does not even allow to read part of the message if it has been tampered with.
PassPhrase:
“A passprase is like a password except it is longer”. In the early days passwords on Unix system were limited to 8 characters, so the term passphrase for longer passwords. Longer is the password harder it is to guess. Nowadays Unix systems use MD5 hashes which have no limitation in length of the password.
Public Key Infrastructure
The Public Key Infrastructure (PKI) is the software management system and database system that allows to sign certifcate, keep a list of revoked certificates, distribute public key,... You can usually access it via a website and/or ldap server. There will be also some people checking that you are who you are... For securing individual applications, you can use any well known commercial PKI as their root CA certificate is most likely to be inside your browser/application. The problem is for securing e-mail, either you get a generic type certificate for your e-mail or you must pay about USD100 a year per certificate/e-mail address. There is also no way to find someone's public key if you have never received a prior e-mail with his certificate (including his public key).
-------------------------thats all for the day. see u soon :) ------------------------------------
-------------------------thats all for the day. see u soon :) ------------------------------------
Labels:
Tech
Monday, August 8, 2011
Future of Computers: 2050
What will the computers of tomorrow be like? Will we still be using keyboards and mice or will we actually live inside a partially digital world? Here’s what we think is in store for the future of computing but share with us your predictions in the comments!
Moore's law predicts that the number of discrete elements on a square-inch silicon integrated circuit will double every two years. While it's not exactly a direct relationship, you can interpret that to mean that computers will double in processing power every two years. That means in the years between 2010 and 2050, computer processing power will double 20 times if Moore's law holds true.
In 2010, IBM introduced the zEnterprise 196 (z196), which boasted a processor capable of running at 5.2 GHz, the fastest commercially available processor at that time. That means the z196 processor ran at 5.2 billion cycles per second. Every instruction a processor executes requires a set number of clock ticks. The more clock ticks a processor squeezes into a second, the more instructions that processor can complete in a given amount of time. That's what we mean when we say a 5.2 GHz processor is faster than a 3.2-GHz processor - the 5.2 GHz microchip is capable of executing more instructions than the 3.2-GHz chip in the same amount of time.
If 5.2 GHz was the top speed in 2010, what will it be in 2050? Assuming engineers can find ways to keep up with Moore's law and processor speed actually doubles every 24 months, by 2050 we'd have a chip capable of running at 5,452,595 GHz, or nearly 5.5 petahertz. It's hard to imagine what kind of applications we could direct such a machine to tackle. Complex computational problems, such as building virtual simulations of the human brain, may become a relatively simple task. Some futurists believe we may even create machines with intelligence far greater than our own. Perhaps those machines could discover ways to improve processing speeds even faster than humans can. Before long, you could have a self-improving device pushing the physical limits of how fast machines can process information.
While this dream of the future is popular among a certain segment of computer scientists and futurists, other people are more skeptical. Perhaps the human mind is far more complex than we understand. Thinking may involve more than just electrochemical messages passed between neurons. Perhaps there's a hormonal element that subtly shapes how we think. If that's the case, it may be that pure computational horsepower won't be enough to create a machine capable of what we consider thought.
Setting aside the artificial intelligence debate for a moment, what might futuristic computers look like? They might actually be invisible. Pervasive computing is a type of technology that incorporates computers into just about anything you can imagine. Buildings, highways, vehicles and even the clothing you wear might have built-in computer elements. Coupled with networking technology, the world of 2050 may be one in which the very environment around you is part of a massive computing system.
In such a world, your digital life and your real life could overlap seamlessly. We see hints of this world in today's technology. There are hundreds of smartphone applications that add a digital layer over our perception of the real world. They might help you navigate around a strange city or discover a new favorite restaurant tucked away in a corner somewhere. These applications still require us to activate programs on mobile devices and use those devices as a lens through which we can see the digital world. In the future, we may be able to accomplish the same thing using glasses, contact lenses or perhaps even ocular implants. Imagine being able to look at the world through one of a million different filters, all of which provide different kinds of information to you instantaneously.
Then again, it's possible that our ingenuity won't be enough to keep up with Moore's law after a few more microprocessor generations. Perhaps our computers will be more mundane and functional. But considering the way they've transformed our world over the last 50 years, I'm willing to bet 2050 will be an exotic, digital era. What do you think?
I want to hear what your predictions are for the future of computing. Please share your ideas in the comments section!!!
Labels:
Tech
Friday, June 17, 2011
Some-OLDIES-> My poem written in 11th standard.
पंडितों की दक्षिणा में करके काट छांट, यात्रा के अतिरिक्त मात्र चौदह रुपये ही बच पाए थे जिसने उसके कदम मदिरालय की ओर उठाए थे. जाने वाला लौट के तो आएगा नही, यही सोच कर उतार लिया सीने में कड़वा पानी.....स्मृति में विगत के चित्र उभरने लगे जब मरते हुए बाप ने अपनी फटी हुई जेब से एक सौ इक्यावन रुपये निकाल कर उसे थमाए थे, कितना दूरदृष्टा था बापू, जानता था जो जीते जी उसे रोटी ना खिला सके वो मरने के बाद पित्र ऋण क्या चुकाएँगे, इनके सहारे रहा तो मेरी अस्थियों को कुत्ते ही चबाएँगे .....
Labels:
Mysterious Life
Wednesday, June 8, 2011
Jan Lokpal Bill- A Brief Review
About JAN LOKPAL BILL:
| Draft Lokpal Bill (2010) | Jan Lokpal Bill (Citizen's Ombudsman Bill) |
|---|---|
| Lokpal will have no power to initiate suo motu action or receive complaints of corruption from the general public. It can only probe complaints forwarded by the Speaker of the Lok Sabha or the Chairman of the Rajya Sabha. | Lokpal will have powers to initiate suo motu action or receive complaints of corruption from the general public. |
| Lokpal will only be an Advisory Body with a role limited to forwarding reports to a "Competent Authority". | Lokpal will be much more than an Advisory Body and have the power to initiate prosecution of anyone found guilty. |
| Lokpal will have no police powers and no ability to register an FIR or proceed with criminal investigations. | Lokpal will have police powers as well as the ability to register FIRs. |
| The CBI and Lokpal will be unconnected. | Lokpal and the anti corruption wing of the CBI will be one independent body. |
| Punishment for corruption will be a minimum of 6 months and a maximum of up to 7 years. | Punishments will be a minimum of 5 years and a maximum of up to life imprisonment. |
Basic Principles of Jan Lokpal Bill :
There should be an institution called Jan lokpal at the centre and Jan Lokayukta in each state.
The following points are being written for Jan Lokpal. However, exactly similar model would be
applicable for states.
Independence of these institutions:
1. These institutions shall be financially, functionally and administratively independent of the
government:
a. Financial independence: Their expenses shall be charged to the Consolidated Fund of
India/state. They shall not need administrative or financial sanctions from any government
agency for making expenditure. The quantum of expenses should be decided in an annual
meeting between the Prime Minister and the Chairperson of Lokpal.
b. Control over their employees: They shall have the freedom to decide the number of
employees required. They will have the power to select and recruit people either from
outside or on deputation or on contract basis or through any arrangement as they deem fit.
2. The Chairperson and members shall not be eligible for appointment to any position in any
organization, which is directly or indirectly funded by any government. It shall also not be
eligible to contest any elections. The total tenure of any member or Chairperson or together as
member and Chairperson shall not exceed five years.
Selection of members and Chairperson of Lokpal and Lokayukta:
3. The process should be completely transparent and participatory. There could be a very broad
based selection committee, which may consist of constitutional authorities, including
representatives from judiciary, bureaucracy and judiciary. This committee may be assisted by a
search committee.
4. The new members should be selected at least three months before the retirement of any
member.
Removal of members and Chairperson of Lokpal and Lokayukta:
5. If prima facie case is made out in a complaint made to the Supreme Court by a citizen against
any member or Chairperson, Supreme Court shall institute a time bound enquiry and advise the
President on the basis of such enquiry. A member or Chairperson of Lokpal may be removed by
the President on the basis of such advice.
Jurisdiction:
6. Lokpal should have jurisdiction the following jurisdiction:a. To receive complaints of corruption under Prevention of Corruption Act against Prime
Minister, all ministers, all members of both houses of Parliament, all bureaucrats and judges
of Supreme Court and High Court; to investigate these complaints and to file prosecution in
appropriate trial courts for prosecution and award of punishment.
b. To receive complaints of misconduct against bureaucrats and recommend appropriate
penalties under conduct rules. However, the recommendation shall be binding on the
government.
c. For complaints against any politician for his/her conduct inside Parliament, Lokpal shall only
investigate the matter on receipt of a reference from Chairperson of either House. After
investigation, the Lokpal shall submit its report to Chairperson, who shall present it in the
House for decision on the same.
7. Lokpal shall not need to seek permission from any other agency for initiating investigation,
enquiry or prosecution. Appropriate amendments would need to be made in Prevention of
Corruption Act and Delhi Police Establishment Act for this purpose.
Powers of Lokpal and Lokayuktas:
8. Lokpal and Lokayukta shall have powers of search and seizure as provided in _____
9. It shall have powers of a civil court to summon and seek production of documents under _____
10. It shall have powers of contempt and imposition of financial penalties to seek compliance of its
orders.
11. It shall have powers to tap telephones under Indian telegraph Act.
12. It shall be deemed to be a police officer.
13. It shall have the powers to recommend, on an annual basis, the number of special courts
required under section 4 of Prevention of Corruption Act, to ensure that the trial in any case is
completed in less than a year. The recommendations shall be binding on the government.
14. It shall have the powers to issue letter rogatory, wherever required, in connection with
investigations of cases under this Act.
15. Notify list of moveable and immoveable assets of accused, if during or at the time of conclusion
of investigations, Lokpal believes that prosecution is likely to be initiated. These assets cannot be
transferred after such notification. Loss to exchequer quantified at the time of conviction, could
be recovered from sale of these assets.
16. Recommend stay of any activity, if during investigations, Lokpal is satisfied that the allegations
against such activity are likely to be sustained.
17. Recommend transfer of any official, if his continuance is likely to adversely affect investigations.18. Powers to issue appropriate directions to prevent destruction of records during investigations,
prevent further further acts of misconduct by a public servant or to prevent the public servant
from secreting the assets allegedly acquired by him through corrupt means.
19. If the allegations are substantiated after any enquiry or investigations, recommend removal of
any minister (barring Prime Minister).
20. Lokpal shall have powers to delegate any of its powers and functions barring those which are
specifically to be performed by the benches of Lokpal.
Internal transparency and accountability of Lokpal:
21. Every complaint shall have to be compulsorily disposed by Lokpal. No complaint could be
disposed without giving an opportunity of being hear to the complainant. If any case is closed,
all records related thereto shall be made public.
22. There shall be complete transparency during investigations also. However, such records, which
could impede the process of investigations, would not be disclosed. But after the completion of
any investigation or enquiry, all records related to a case, shall be made public.
23. Lokpal shall publish, every month on its website, the status of cases, received, disposed, closed,
reasons for closure and list of cases pending.
24. Any complaint against a staff of Lokpal shall be enquired into within a month of its receipt and if
found correct, the staff shall be summarily dismissed from the job. If any criminal case is made
out, the same shall be pursued.
Punishments and recovery of loss to the government:
25. At the time of conviction, the court shall make an assessment of the loss caused by the accused,
which shall be recovered from them.
26. The minimum punishment shall be raised to one year of rigorous imprisonment and maximum
should be raised to life imprisonment.
27. Punishment shall be higher if the status or rank of accused is higher.
28. If the beneficiary is a business entity, five times the loss caused to the government shall be
recovered. The recovery may be done from the assets of that entity or the personal assets of its
directors.
29. If any person obtains any benefit from the government in violation of any rules or laws, that
person along with concerned public servants shall be deemed to have indulged in corrupt
means.
Whistleblower protection:30. Lokpal shall be responsible for providing protection against professional or physical threat or
victimization to whistleblowers, whether within or outside the government.
Public grievances with vigilance angle:
31. Every department shall prepare a citizens charter mentioning which work will be done by which
officer in how much time. Each department shall also designate the Head of the Department or
a sufficiently senior officer as Public Grievance Officer (PGO). Violation of citizen’s charter will be
dealt by PGO, who will be required to get the work done in 30 days. If PGO also fails, the
grievance will go to Vigilance Officer (who will be part of the Lokpal) and the grievance will be
deemed to have a vigilance officer. The vigilance officer shall get the work done in next 30 days,
impose penalties on the guilty officers which will be paid as compensation to the citizen and
proceed with enquiries of misconduct against guilty officers.
CBI, CVC and departmental vigilance:
32. The anti-corruption wing of CBI, the CVC and departmental vigilance wings of all departments
will be merged in Lokpal.
Declaration of annual property statements:
33. Each bureaucrat, politician and judge would be required to submit his/her statement of
moveable and immoveable assets on an annual basis, which will be put on a website.
34. If any asset is subsequently found to be owned by a public servant, which was not declared, it
would be deemed to have been obtained through corrupt means.
35. If any asset is subsequently found to be in possession of any public servant, it shall be deemed to
be owned by him/her unless he proves otherwise.
36. After each elections, the Lokpal shall verify the assets declared by each candidate with his
declared sources of income in his tax returns. Those undeclared shall be investigated against.
CAG to forward cases of corruption:
37. CAG, after its report has been laid in the Parliament, shall forward such cases to Lokpal, where it
feels that an offence under Prevention of Corruption Act is made out. Such cases shall be
investigated by Lokpal.
Power to make Rules:
38. No rules shall be made without the approval of Lokpal. Lokpal shall have power to make rules
and regulations with respect to its own functioning.
Transparency and applicability of Right to Information Act to Lokpal:
39. All records of Lokpal shall be open barring the following:a. Such portions of any records which if released during any ongoing investigations, could
impede the process of investigations. However, after completion of investigations, they
would be disclosed.
b. Such records which could affect national security or
c. Such records which would disclose the identity of a whistleblower and could compromise
his/her security.
Fines for frivolous complaints:
40. If anyone makes a complaint which lacks any evidence or basis and is held by Lokpal to be meant
only to harass someone, the complainant shall be fined. However, merely closure of a case due
to lack of evidence shall not be held against a complainant.
Lokpal bills were introduced in 1971, 1977, 1985, 1989, 1996, 1998, 2001, 2005 and 2008 but all failed to pass,a long span of 12 Prime Ministers.
After RTI we are moving towards ROR (Rights of Rejection) to avoid Vote-Banking.
Next topic of this blog might be about Rights of Rejection. :)
STAY AWAKE STAY AGILE....
Labels:
Politics
Friday, June 3, 2011
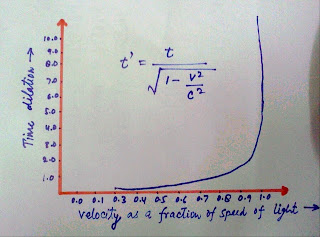
Time Dilation and Relativity
After watching this video lots of questions may popping out from your mind, though I'd also faced the same dilemma "what the crap, how the time can slow down? in my school days I made several time vs "Any dimension" graphs, but in none of them I saw or even dare to took the time in negation. but as time passes and I get involved in my IIT coaching :) that was the time for one2one with the first torture of my studies viz I.E. Irodov :(
First time there I got TIME as a dimension (fourth). lots of confusions how to imagine time as a frame of reference and put it into real time physical platform....look similar of trying download a movie using torrent containing 1GB mirror in a dial up BSNL connection (specially in a cyber cafe of Kanpur city in the days of year 2k :P)
anyways lets come into the focus:
What is Time Dilation?
One of the most enthralling aspects of Relativity is its new understanding of time.However, time dilation is all but surrealistic.As we all know the speed of light is constant but time cannot be constant. In fact, it doesn't make sense to speak of time as being constant or absolute, when we think of it as one dimension of spacetime. Special Relativity states that time is measured according to the relative velocity of the reference frame it is measured in. Despite of the simplicity of this statement, the relativistic connection between time and space are hard to fathom. There are numerous ways to illustrate this:
The four dimensions of space-time.
In Relativity the world has four dimensions: three space dimensions and one dimension that is not exactly time but related to time. In fact, it is time multiplied by the square root of -1. Say, you move through one space dimension from point A to point B. When you move to another space coordinate, you automatically cause your position on the time coordinate to change, even if you don't notice. This causes time to elapse. Of course, you are always travelling through time, but when you travel through space you travel through time by less than you expect. Consider this example:Time dilation; the twin paradox.
There are two twin brothers. On their thirtieth birthday, one of the brothers goes on a space journey in a superfast rocket that travels at 99% of the speed of light. The space traveller stays on his journey for precisely one year, whereupon he returns to Earth on his 31st birthday. On Earth, however, seven years have elapsed, so his twin brother is 37 years old at the time of his arrival. This is due to the fact that time is stretched by factor 7 at approx. 99% of the speed of light, which means that in the space traveller’s reference frame, one year is equivalent to seven years on earth. Yet, time appears to have passed normally to both brothers, i.e. both still need five minutes to shave each morning in their respective reference frame.Time in the moving system will be observed by a stationary observer to be running slower by the factor t':
As it can be seen from the above function, the effect of time dilation is negligible for common speeds, such as that of a car or even a jet plane, but it increases dramatically when one gets close to the speed of light. Very close to c, time virtually stands still for the outside observer.
As it can be seen from the above function, the effect of time dilation is negligible for common speeds, such as that of a car or even a jet plane, but it increases dramatically when one gets close to the speed of light. Very close to c, time virtually stands still for the outside observer.
Time expands, space contracts:
Interestingly, while time expands from the perspective of the stationary observer, space contracts from the perspective of the moving observer. This phenomenon is known as Lorentz contraction, which is exactly the reciprocal of the above time dilation formula: l'=l*sqr(1-v²/c²). Thus the space traveller passing by Earth at a speed of 0.99c would see it's shape as an ellipsis with the axis parallel to his flight direction contracted to a seventh of its original diameter. That is of course, if he sees it at all, given the enormous speed. Therefore, space travel is shortened with the velocity of the traveller. A journey to the 4.3 light-years distant Alpha Centauri C, the closest star to our Sun, would take only 7.4 months in a space ship moving at 0.99c.The effect of time dilation has been experimentally confirmed thanks to very precise caesium clocks that can measure extremely small periods of time. Unfortunately, time dilation is completely outside of human experience, because we have not yet devised a way of travelling at speeds where relativistic effects become noticeable. Even if you spent your whole life in a jet plane that moves at supersonic speed, you would barely win a second over your contemporaries on the ground. And, not even today's astronauts can perceive the Lorentz contraction. Imagine you are a cosmonaut on board of space station Mir, moving at 7700 meters per second relative to Earth. Looking down upon Europe from space, you would see the entire 270 kilometre east to west extent of Switzerland contracted by a mere 0.08 millimetres.
Can we travel at the speed of light?
The hope that one day mankind will be able to travel at near-to-speed-of-light velocities seems farfetched, because of the incredible amounts of energy needed to accelerate a spacecraft to these speeds. The forces are likely to destroy any vehicle before it comes even close to the required speed. In addition, the navigational problems of near-to-speed-of-light travel pose another tremendous difficulty. Therefore, when people say they have to hurry in order to "win time", they probably don’t mean it in a relativistic way.
Life in a space-time cubicle.
From Relativity we learn that time and space is seemingly independent of human experience, as the example of time dilation suggests. Since our own perception of time and space is bound to a single reference frame, time appears to be constant and absolute to us. Physics teaches us that this is an illusion and that our perception deceived us within living memory. Thanks to Einstein, we are now able to draw relativistic spacetime diagrams, compute gravitational fields, and predict trajectories through the four-dimensional spacetime continuum. Still, we are hardly able to visualise this spacetime continuum, or deal with it in practical terms, because human consciousness is bound to the human body, which is in turn bound to a single reference frame. We live within the confinements of our own spacetime cubicle.Considering that in Relativity, spacetime is independent of human perception, the Kantian understanding of space and time as a priori particulars seems to be obsolete. They are no longer properties of perception, but properties of nature itself. But, there is more trouble looming for Kant. Relativity stretches the distinction between phenomenal reality, i.e. that which can be experienced, and noumenal reality, i.e. that which is purely intelligible and non-sensory, to a degree where these concepts almost appear grotesque. For example, the question arises, whether time dilation falls into the noumenal or phenomenal category? Since it can be measured, it must be phenomenal, however, since human perception is bound to a single reference frame, it must also be noumenal. The distinction between noumenon and phenomenon is thus blurred and possibly invalidated.
We can attempt to imagine relativistic models with the help of appropriate mathematical models, but cannot experience it directly, at least not until someone builds a near-to-speed-of-light spacecraft. I personally thanks to Einstein :) (looks funny), we are able to look beyond the phenomenal reality of space and time, and we understand that there is more to it than commonsense perception tells us. In a way, Einstein has freed our minds from the spacetime cubicle.
Labels:
Tech
Subscribe to:
Comments (Atom)